Being the Information Security Manager at a startup, I have to be able to demonstrate to our CEO that we have acted on critical vulnerabilities. It also means that I have to be quick and efficient. Here's how I assess all of our third parties under 60 seconds using our platform:
How JustProtect assesses 100% of our third parties
Dec 14, 2021 1:40:26 PM / by Bryan "SOC" Urias posted in compliance, vendor, Risk Assessor, Security, Log4j
Why the SolarWinds Lawsuit should concern CFOs as well as CISOs
Aug 20, 2021 10:00:00 AM / by Haley Keitel posted in cybersecurity, Security, CISO, CFO, data breach
SolarWinds is facing a continued lawsuit from investors that has specifically named the CFO and now the CISO, as a result of their lack of disclosure controls and systems surrounding their cybersecurity risk management following a major breach.
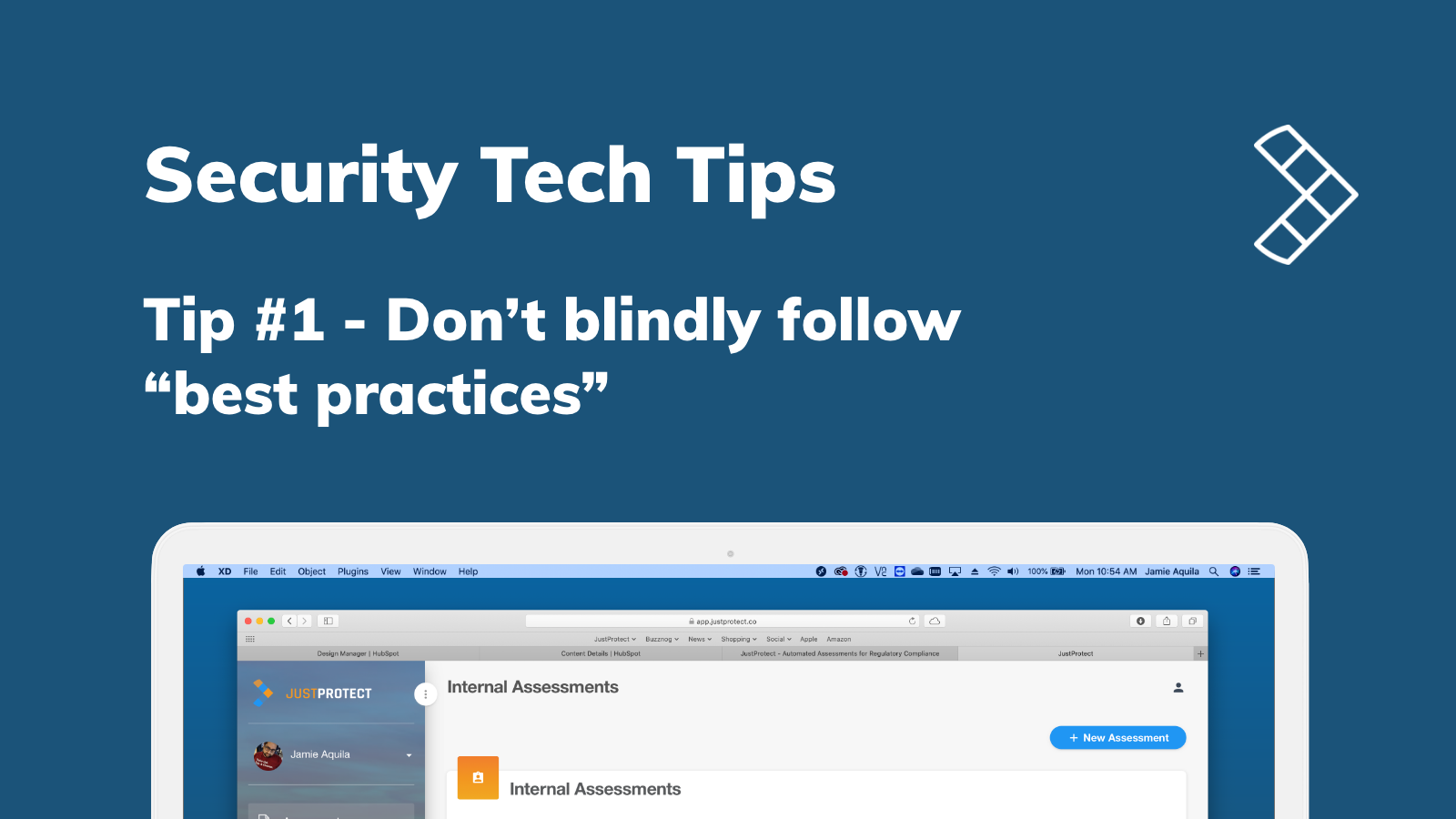
10 tips for cybersecurity professionals
Aug 19, 2021 2:00:00 PM / by Haley Keitel posted in cybersecurity, Strategy, Security, CISO
We want to equip you with tips on how to markedly improve efficacy in your role. While these tips are general enough to apply to anyone in security, we find that they are geared towards anyone fresh to the industry or new in a cybersecurity role
Read on for our top ten tips for cybersecurity professionals like yourself.
3 ways to simplify cybersecurity and risk management without the anxiety
Jul 21, 2021 5:00:00 PM / by Haley Keitel posted in compliance, cybersecurity, 3rd party, Risk Assessor, Security, privacy
Here are three quick ways to simplify your risk management processes without increasing your anxiety or your costs.
Why a company like yours doesn't need a fully formalized ISMS.
Jul 7, 2021 1:21:01 PM / by Bryan "SOC" Urias posted in cybersecurity, Strategy, dashboards, Security
An Information Security Management System (ISMS) is simply a framework for information security practices within your organization. You may immediately jump to think about a full set of policies and procedures, several stacks of network appliances, certifications, and an endless number of hoops to jump through.
The good news is that you don’t have to start there, the most important step is not the first step or the last step. It’s the next step. You can simply begin using risk-based strategies to build your ISMS one layer at a time.
First American Financial Corporation Enforcement
Jun 30, 2021 3:19:25 PM / by Haley Keitel posted in compliance, cybersecurity, Policy, Security
First American Financial Corporation (FAFC) is facing the first-ever penalty from the SEC in the form of a cease-and-desist order and civil fines, as a result of their lack of disclosure controls and systems surrounding their cybersecurity risk management.
How assessments can prevent ransomware
Jun 21, 2021 4:48:04 PM / by Haley Keitel posted in cybersecurity, assessments, Security, ransomware
Ransomware is not isolated to tech companies, which is clearer than ever given the attacks this year. In a recent interview with Now This, our CEO Vikas Bhatia, discussed the fundamentals of these attacks and how companies across industries can better prepare by utilizing a third-party risk management plan.